Microsoft Free Antivirus For Xp Review
The Best Free AV for 2016. You need antivirus software. technicians who review its reports and even step in to gives you antivirus.
Video embedded Microsoft Security Essentials 4 review Free Anti-Malware Microsoft Security Essentials 4 This compares with 14.5 for Avast Free Antivirus.
Jan 26, 2011 Microsoft Security Essentials offers decent free antivirus protection with the benefit of the Microsoft name. However, other free antivirus XP test.
Viruses and other malicious software with this free Microsoft Safety Scanner for existing antivirus subscription to Microsoft Security.
It s FREE. Free Antivirus for Microsoft Windows 8, 7, Vista and XP. Our antivirus products also offer strong protection for Microsoft s older operating systems.
Consumer security software providers If you re Should you wish to explore alternatives to the already installed or available Microsoft Avast Free Antivirus.

The bottom line: Microsoft Security Essentials 2 will protect you, and it will generally do it well. However, its impact on system performance could be improved, and it s still a bit light in the tool belt.
Now in its second iteration, Microsoft Security Essentials MSE debuted as the lightweight, cloud-based successor to the paid security suite Live OneCare in 2009. Version 2 introduces deeper hooks into Internet Explorer and the default firewall in Vista and Windows 7. Security Essentials has begun to mature, although it s still rough at the edges.
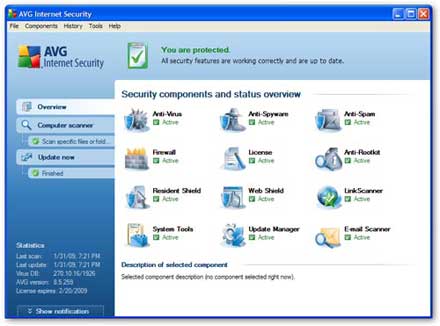
Microsoft Security Essentials 2 photos
It takes very little effort to get going with MSE. Microsoft politely does not opt you in to the program s customer experience improvement program; you must choose to opt in or stay out of it before you can finish the installation. It also lets you choose whether to run the Windows Defender firewall, and whether to run a scan once installation is complete, although both of those are opt-out.
Overall, the installation time ran around 4 minutes on our test computer. That s not as blazing fast as some of the paid suites, which can complete installation in less than 60 seconds, but it is respectable for a free program.
MSE 2 s interface adopts a different color scheme than the previous version, going for various shades of gray to replace the vibrant blue and white look. It doesn t pop as much, but it also looks far less like a Windows XP relic.
For those unfamiliar with the design, MSE has four tabs across the top. The Home tab contains your security status and scan options, and you can run a Quick Scan, Full Scan, or Custom Scan. A link at the bottom of the pane lets you change the scheduled scan.
The second version of Microsoft Security Essentials changes its plumage to gray, and adds better heuristic detections and deeper hooks into the Windows firewall.
Screenshot by Seth Rosenblatt/CNET
Update is where you manually get new virus definition files and program upgrades, History logs only detected threats, and Settings is where you go for advanced tweaking. The program looks simple, but don t be deceived: there are quite a few advanced options in Settings--just not as many as many competitors offer. Security Essentials uses labels imported from OneCare: green for all good, yellow for warning, and red for an at-risk situation.
Under the clean and uncluttered interface, Security Essentials wraps up antivirus and antispyware engines, rootkit protection, and real-time detection courtesy of Microsoft SpyNet, the unfortunately named cloud-based service that anonymously compares file behavior across computers running various Microsoft operating systems.
SpyNet was introduced in Windows Vista and extended to Windows 7, but Microsoft Security Essentials is the only way to access the network in Windows XP. Unlike other security vendors that allow customers to take advantage of the benefits of their behavioral detection engines while opting out of submitting information, there s no way to do that with SpyNet.
Well, it s mostly anonymous. You can choose between two SpyNet memberships. The basic membership submits to Microsoft the detected software s origins, your response to it, and whether that action was successful, and the advanced membership submits all that plus the location on your hard drive of the software in question, how it operates, and how it has affected your computer. Both basic and advanced versions warn users that personal data might be accidentally sent to Microsoft, although they promise to neither identify nor contact you. New in version 2 is the option to opt out of contributing to SpyNet while still receiving the benefits of crowd-sourced security.
When you install MSE 2, it will automatically run a scan unless you opt out. Note that it will not consider your computer secure until that first quick scan has completed.
Microsoft Security Essentials 2 uses both definition-file and real-time defenses against viruses and spyware, and also offers rootkit protection. Along with the quick scan and the full scan, there s a Custom scan option that lets users select specific folders or drives to scan. It doesn t allow for customizing the type of scan used. For example, you re not going to be able to choose to scan only for rootkits or heuristics, as you can with other security programs. However, you can set USB keys and other external devices to automatically get scanned. The program installs a context-menu option for on-the-fly scanning in Windows Explorer, too.
The Update pane manages the definition file updates, with a large action button, and History provides access to a spreadsheet-style list of All detection items, your Quarantine, and items you ve Allowed to run. Although it s a basic layout, this no-frills approach to security has proven appealing to people who are overwhelmed by more detailed security choices.
New in version 2 is integration with Internet Explorer so that downloads get scanned, and Windows firewall hooks so that your personal security net is tighter. For Windows 7 and Vista users, the Windows Filtering Platform that those two operating systems come with gets a boost from a new network inspection feature.
The Settings window allows you to further customize the program by scheduling scans, toggling default actions to take against threats, adjusting real-time protection settings, creating whitelists of excluded files, file types, and processes, and choosing from the aforementioned SpyNet options. There s also an Advanced option that is still fairly basic: here you can set Security Essentials to scan archives and removable drives, create a system restore point, and expand user rights to allow all users to view the History tab.
A nice feature in the scheduler forces MSE 2 to be respectful of your computer s processor usage.
Security Essentials comes preconfigured to run a scan weekly at 2 a.m., when Microsoft thinks your system is likely to be idle. New malware signatures are downloaded once per day by default, although you can manually instigate a definition file update through the update tab. Attachments and downloaded files will be automatically scanned by Security Essentials.
Help is only available in the form of the standard offline Help manual that comes with all Microsoft programs. There s nothing fancy here.
MSE abandons the additional heft of a firewall, performance tuning, and backup and restore options to focus on core security. However, the new version does include a system restore option, to back up your computer before you remove any detected malware. Most of the changes in MSE 2 are under the hood, but it s still a worthwhile program in terms of features, especially on lower-powered Netbooks.
Microsoft Security Essentials occupies a slightly different space than the rest of the security programs because it s the only one published by Microsoft, and, remarkably to some, it doesn t suck. Benchmarks by independent third-party efficacy testers and CNET Labs discovered that the program has uneven performance. Read more on how CNET Labs benchmarks security software.
Unprotected system 42.5 11.28 n/a 917 180 780 4,795 Microsoft Security Essentials 2 54 18 1,560 1,038 201 800 4,790
All tests measured in seconds, except for Cinebench. On the Cinebench test, the higher number is better.
AV-Test.org certified MSE 1 during one test this year, and then refused to certify it during a test several months later. When tested on Windows 7 in the second quarter of 2010, MSE 1 earned certification with a 15 out of 18 score. It achieved 4 out of 6 in the Protection category, 4.5 out of 6 in Repair, and 5.5 out of 6 in Usability, where the minimum required for certification was 12. However, when tested on Windows XP in the third quarter of 2010, AV-Test.org did not pass MSE 1. The program earned 3 out of 6 in both Protection and Repair, and 5.5 out of 6 in Usability. Given the more advanced native security in Windows Vista and Windows 7, this could indicate that Microsoft s own security program is unsuitable for its older operating systems.
On the other hand, AV-Comparatives.org awarded MSE 1 an Advanced certification in November 2010 for its retrospective/proactive test, finding the program to have very few false positives.
Those results don t come cheaply, as far as system performance is concerned. CNET Labs benchmarks put MSE 2 at the far slower end of the scale, with a bigger impact on system performance in general than most other security options. System start-up was 11.5 seconds slower than on an unprotected PC, and system shutdown was more than 6 seconds slower whereas most suites affected the system by 2 to 4 seconds.
MSE 2 s impact on the MS Office, iTunes decoding, media multitasking, and Cinebench tests was generally unimpressive. The program did very well in the Cinebench test, but in others its results were more middle-of-the-road.
Virus scan times were also slow compared with the competition. MSE 2 took 26 minutes to finish a full scan, and nearly 2 hours on a real-world computer. The 2-hour time is slow, although not the slowest out there. The first quick scan performed at installation took 4 minutes, which is a competitive time for that type of scan.
Security Essentials is basically a good set-it-and-forget-it security program, but if you want more options and better results from a lightweight security option, Panda Cloud Antivirus Free Edition 1.3 is the safer bet. Microsoft Security Essentials beta.
Find out how Microsoft Security Essentials helps you can help protect them with Microsoft System Center 2012 Endpoint Free antivirus.
How good is Microsoft s free antivirus software. Microsoft gave an end date for XP, then turned around and extended it, then when that date neared extended it.
Westward Kingdoms Final Crack

Our philosophy is to provide the highest quality of customer service, nothing less. We are committed through education, creativity, and passion to bring unsurpassed.
Sample Results From Member Downloads
DownloadBound.com provides direct download access to the most recent releases. We have literally hundreds of thousands of direct downloads including categories such as: software, movies, games, tv shows, adult movies, music, ebooks and much more. Our members download database is updated daily.
Take advantage of our limited one time 3 offer and gain special member access to unlimited direct downloads. That s right. You can try our unbeatable service and see how brilliant it is. This special offer will expire soon. Take the DownloadBound tour today for more detailed information.
Westward Kingdoms Final Download Search Tips
To create more accurate search results for Westward Kingdoms Final try to avoid using keywords like crack, serial, key, unlock, activation, code, keygen, full, version, cracked, etc.
Downloads like Westward Kingdoms Final may often include a crack, keygen, serial number or activation code to make it the full version. If it does then it will be found in the full download file itself.
The word crack in this context means the action of removing the copy protection from software. A crack is a program, set of instructions or patch used to remove copy protection from a piece of software or to unlock features from a demo or time-limited trial. There are also crack groups who work together in order to crack software, games, etc. If you search for Westward Kingdoms Final Crack, you will often see the word crack amongst the results, which implies it is the full version download of the product.
The word serial in this context means a unique number or code which identifies the license of the software as being valid. All retail software uses a serial number or activation key of some form, and the installation often requires the user to enter a valid serial number to proceed. A serial can also be referred to as a CD Key. When you search for Westward Kingdoms Final Serial, you may find the word serial amongst the results. This usually means your download includes a serial number.
The word keygen means a small program that can generate a cd key, activation number, license code, serial number, or registration number for a piece of software. Keygen is a shortcut word for Key Generator. A keygen is made available through crack groups free to download. When writing a keygen, the author will identify the algorithm used in creating a valid cd key. They can then incorporate this into the keygen. If you search a download site for Westward Kingdoms Final Keygen, this often means your download includes a keygen.

Found 6 results for Westward Kingdoms Final Activation Code. Full version downloads available, all hosted on high speed servers.
2010 English PC Developer Publisher by: Sandlot Games 75.8 MB
When two young spoiled heirs to the throne are banished from the comforts of their royal realm, they are tasked with traveling to three neighboring kingdoms, restoring their greatness, and demonstrating to their father, the king, that they are the rightful heirs to the throne.
Help Prince Fenwick and Princess Catherine roam the countryside as they seek the guidance of friendly Kings, Countesses, Dukes, and loyal subjects. Navigate dangerous forests teeming with ogres, barbarians, wizards, dragons, and fearsome Black Knights, as you uncover the truth behind the royal banishment in Westward Kingdoms.
38 buildings, all-new upgrades and features
Train skilled workers to run advanced buildings
New enemies determined to stop your progress
Unlock secret items and characters hidden throughout Westward Kingdoms
Westward Kingdoms Final.rar rapidshare megaupload hotfile, Westward Kingdoms Final.rar torrent download, Westward Kingdoms Final.rar full free download, Westward.

Westward Kingdoms PC/ENG/FINAL rapidshare megaupload free torrent, rar Zip Highspeed torrent download included crack, serial, keygen, cdkey, 2014, 2015.
Westward Kingdoms Final returned 5 download results. Full version downloads hosted on high speed servers.
Direct downloads for Westward Kingdoms Final. Includes: Crack Serial Keygen if applicable. New links added daily. Last updated: 23-Dec-2015.
Anschutz Match 54 Serial Numbers
2, What is the difference between the two actions Match 54 and Match 64. 7, The serial number of my old rifle is fixed on the barrel not on the reciever.


I was looking at a 1977 Match 54 it does have the Super Match Action. What I The serial number should end with an X. Most were very good.
Mar 13, 2008 - I just acquired an Anschutz Match Model 54, serial number 61725J.G. Anschutz GMBH, Waffenfabrik U1m/D Germany stamped on the barrel.

Manufacturer/Trademark - Anschutz Model/Configuration - MODEL 1413 SUPER MATCH 54. Serial Number – mfg. circa. additional info -. 22 LR cal..
Anschutz began production of the Match 54 in 1954. From this proof date the serial number should be somewhere around 20,000. Anschutz Dating an Anschutz barrel action11 postsSep 11, 2013Anschutz Modell 1411/1413 Match 5420 postsJul 12, 2012Anschutz Model Nomenclature14 postsMay 18, 2012Anschutz Mod 54 Bolt availablity13 postsOct 14, 2011More results from www.targettalk.org54 super match Archive - RimfireCentral.com Forumswww.rimfirecentral.com/forums/archive/index.php/t-16842.htmlCachedSimilarJan 15, 2003 - 23 posts - 7 authors Archive 54 super match Anschutz. The serial number should be on the action and the first two digits designate the year made. Is the bolt Anschutz Super Match 5421 postsFeb 15, 2014Anschutz 54 match Rifle. .34 postsMay 18, 2009will the oldest Anschutz step forward please.90 postsNov 28, 2004Anschutz Match 54 Trigger5 postsMay 6, 2003More results from www.rimfirecentral.comAnschutz Match 54 vs 1407 serial numbers - Rimfire www.rimfireshooting.com Rimfire Rifles AnschutzCachedSimilarMar 1, 2013 - 8 posts - 5 authorsAnschutz Match 54 vs 1407 serial numbers - posted in Anschutz: Hi, I am Alberto from Italy. I like very much rimfire rifles and I already got a.
Our FAQ sections contain a detailed list of the frequently asked questions of our customers.
Does ANSCHÜTZ give information on the production year of firearms.
We need a lot of time to determine the age of a firearm with the help of the serial number. This is the reason why we only give this information to authorities or for a fee. However, every firearm owner can determine the approximate age of his gun with the help of the proof house stamp on the barrel of our firearms. The production years mentioned below are only approximate values and only mirror the common procedure representative for the referring period. Exeptions are possible. It might therefore be that even after the year 1968 there is only the production year imprinted on the barrel but no code.
Various proof test stamps approximate year
Up to approx. 1958 only the proof test stamp and the kind of ammunition was imprinted on the barrel.
From approx. 1958 to approx. 1968 apart from the proof test stamp also the last two digits of the referring year were imprinted on the barrel.
Since approx. 1968 the year of manufacture is coded. The code for determining the age is as follows:
0 A; 1 B; 2 C; 3 D, 4 E; 5 F; 6 G; 7 H; 8 I/J; 9 K
The year of proof testing is described by the last two digits of a year, i. e. that a firearm with the letters AF was officially proof tested in the year 2005 05.
Since 2014 the Federal Eagle as proof test stamp is replaced by the letters CIP.
If you nevertheless need our help to determine the age of your ANSCHÜTZ rifle or pistol we will render this information for a fee. Please fill in the form below for this purpose.
Since the end of 2006 the installation date date of assembly of the LaserPower rifle is marked on the stock mentioning the month and the year.
ANSCHÜTZ GmbH Co. KG does not guarantee that the information on these pages is up-to-date, accurate and complete, or that it can be accessed without trouble at any time. ANSCHÜTZ GmbH Co. KG, Ulm, Germany, is not responsible for any contents of menues or sub menues of direct or indirect links to other pages and explicity dissociates itself from it herewith. By activating the link you leave the ANSCHÜTZ internet offer. Please be aware that diverging regulations can be applicable to the services of third parties, especially with regard to data privacy protection.
Standard markings are present, with a matching serial number on the bolt face. Fitted with a Anschutz Model 54 Match Single Shot Bolt Action Rifle. Click on.
Does ANSCHÜTZ give information on the production year of firearms. need a lot of time to determine the age of a firearm with the help of the serial number.
How To Crack Password Protected Winrar Files
How to Crack WinRAR Password Protected Files
InShortViral: Today we are here with a cool method for How To Unlock Password Protected WinRAR Files.
WinRAR is a tool to compress large files into smaller size. And sometime when you download any winrar file from internet sometime they are protected with a password and can t get open without its password. And to get it you get through some shitty surveys that you might not interested to do. So to overcome this we have a way to unlock password protected RAR files. For that you have to follow the complete guide discussed below.
Also Read: How To Protect A Folder With Password In Windows
The method is quite simple using a tool that will refix your password and you can open the locked winrar files easily. So proceed with the simple steps below to unlock your RAR files.
Also Read: How To Crack Windows 7,8,10 Password
Steps To Crack Password Protected WinRAR Files:
First of all download and install the too iSumsoft RAR Password Refixer in your windows PC.
Now launch the software and you will see screen like below.
Click on open button there and locate your rar file that is password protected.
Now there select the attack type that you want to perform to unlock your rar files. If one not work keep on trying other one.
Now just click on start button there.
Process will start and your password will be refixed with a new one that you will get on the screen from this tool.
Use the password and you are done with opening password protected RAR files.
Also Read: How To Crack Patch Any Android App By Lucky Patcher
So above is all about Unlock Password Protected WinRAR Files. With the above guide you will be able to open any RAR file that is password protected by any tool. And you can access all the important files locked inside the file. Hope you like this cool trick, do share this with others too. Leave a comment below if you have any related queries with this.
Receive Notifications of New Posts by E-mail
How to unlock password protected. rar files without password.. Discover answers on How to unlock password protected. rar files without password.. Post you.


BEFORE WE BEGIN. For the purposes of cracking, opening, extracting, or unlocking password protected or encrypted ZIP, PDF, RAR, XLS, and XLSX files, we will be.

Winrar Password Remover Crack Keygen is specially for the professionals. Winrar Password Remover Serial Number uses to open the RAR files which has locked.
- Steps To Crack Password Protected WinRAR Files: First of all download and install the too iSumsoft RAR Password Refixer in your windows PC. Now launch the.
- Short Bytes: Losing/forgetting your WinRAR password could be a headache. So, here, I m going to tell you this simple method of how to crack WinRAR password.
- Nov 05, 2014 Download script here : https://github.com/RohitSaxsena/Crack Download dictionary list here : cr am.
- WinRAR, much like WinZip, compresses files and supports a wide array of file extensions such as . zip and . rar etc. When you create a file archive with WinRAR.
- Sep 15, 2013 With this Tool you can Crack Passwords form Winrar/Zip and any Folder File. The Winrar Password Unlocker is easy to use and very effective. I get.
Free Antivirus Software For Windows Xp 2000
AVG Anti-Virus Free Edition is a reliable antivirus and antispyware protection for Windows available for free download.The Screenshot displays AVG fab.
TechGenie Free Antivirus; Home Solutions. iYogi Corporate; Business Solutions; Before installing an antivirus software on the Windows 2000 operating system.
I m running Windows 2000 Pro and the latest version of AVG 9.0 does not support it. As a pensioner, I cannot upgrade Windows every time Microsoft brings out a new.
This maintenance release updates ClamAV scanning engine and fixes these issues:
ClamWin is a Free Antivirus program for Microsoft Windows 7 / Vista / XP / Me / 2000 / 98 and Windows Server 2008 and 2003.
ClamWin Free Antivirus is used by more than 600,000 users worldwide on a daily basis. It comes with an easy installer and open source code. You may download and use it absolutely free of charge. It features: High detection rates for viruses and spyware;Scanning Scheduler; Automatic downloads of regularly updated Virus Database. Standalone virus scanner and right-click menu integration to Microsoft Windows Explorer; Addin to Microsoft Outlook to remove virus-infected attachments automatically.
The latest version of Clamwin Free Antivirus is 0.97.3
Please note that ClamWin Free Antivirus does not include an on-access real-time scanner. You need to manually scan a file in order to detect a virus or spyware.
ClamWin Free Antivirus is a free software project.
How can you help: Submit undetected virus and spyware samples. Test the latest release, find and submit bugs and feature requests. Improve the documentation. Promote ClamWin Free Antivirus on the Internet and in the press. Link to clamwin.com on your web site to let other people know about it and improve clamwin.com rankings If you are a C or Python developer and have some time to spare you may join the ClamWin Free Antivirus Project and help to improve it
Or please click here to make a donation
and support further development of ClamWin Free
Free Scan Registry Mechanic Cleans, Repairs, and Optimizes Your PC
Problems with the Windows registry are a common cause of Windows crashes, slow performance and error messages. Registry Mechanic is an advanced registry cleaner for Windows that can safely clean, repair and optimize your registry in a few simple mouse clicks. Click on the link above for a free download.
Remove Spyware. Free Download.
Spyware Doctor is a top-rated malware spyware removal utility that detects, removes and protects your PC from thousands of potential spyware, adware, trojans, keyloggers, spybots and tracking threats. Click on the link above for a free download.
Jul 12, 2010 Hi piggypopo, please be informed that Windows 2000 not server is supported operating system by AVG 9.0 Free. AVG 9.0 Free installation file could be.
Avast. Free Antivirus is the freeware version of Avast. antivirus software available to Microsoft Windows and Linux users, while Avast. Pro Antivirus is offered to.
Avira Free Antivirus 2015. Avira AntiVir Personal is a security software that keeps your personal computer clean and safe. Its advanced features give full protection.

ClamWin is a Free Antivirus program for Microsoft Windows 98/Me/2000/XP/2003 and Vista. ClamWin Free Antivirus comes with an easy installer and open source code.
This article defines Sophos Anti-Virus for Windows 2000. Products; Labs; Partners; Company; Download; Documentation ; Training; Contact; Free Trials.
Open source GPL virus scanner
The most downloaded Antivirus Software software, including McAfee AntiVirus Plus, McAfee Total Protection, and Avast Free Antivirus 2016. Windows 2000.
Lobster A200 Vista Driver
We ll help you find a nice, safe and short bicycle route in London and around. Many cycle search preferences, print and GPX exports. Based on OpenStreetMap data.
Infinity box - Unlocking equipment for Chinese mobile phones, LG, CDMA, Nokia, Motorola, Sony Ericsson, Samsung.
Infinity box plus combo 2 in 1 box pinfinder 46 pcs unlock cable set.
Download torrents
Amazon Toys: More Than Your Average Toy Store. Amazon s Toys Games Store features thousands of products, including dolls, action figures, games and puzzles.
Each user receives a different part, which in turn, after saving it on a computer begins to be distributed. If communication is interrupted by one of the distributers, the program chooses another one and the process continues. In addition, the user with the greatest speed distribution is always selected as a dealer. There is nothing complicated about it, that s just sounds a little confusing. After the first experience with the program, you will understand everything. In addition, BitTorrent-Client undertakes almost all the important functions for downloading and distributing torrents.
How does a BitTorrent-Client work.
To download a torrent, you need to find a special server-torrent tracker. We can recommend you as one of the easiest and understandable sites of such kind. On this server, you select the file and start quick download. Of course, physically, there are no files on the server itself. All of them are located on the computers of other users and server shows just a list of files. The very same server coordinates the distribution of the files from one users to another. If it happens so that no user is distributing user is online, then downloading torrents is impossible, because in fact there is nowhere to take it. If this happens, try to free download torrent in the evening or at night, usually at this time there are more members that are active. That s the way the answer to another question: where to download the torrent. And the answer is - of course, from a site or server tracker, like slowtorrent.com. Download torrent.
It is also worth remembering that the torrent client runs in the background and consumes very few resources of your computer. So you can safely work or study, while download torrent online. And you can put files to download any number as long as there is enough of hard disk memory.
Now, we will have practical training on how to download torrent. To begin with, get in the vast network of Internet software torrent client. Next, select yourself any torrent tracker, register and select the file that you would like to download.
One of the most popular BitTorrent-clients is μTorrent. It is easy to use and not greedy for computer resources. Small footprint, quick to install, does not require any pre-setting, that is immediately ready for use.
Now let s look where to download torrent files. Search torrent files on torrent trackers, special sites and servers, where users share files. Some trackers might be only a list of files on the other, for an individual file can be assigned a separate page, with the most detailed description of it. It is preferable to use the latter, especially for beginners. Some torrent trackers require registration, others do not require it.
So, how to free downloads torrents. If the site has a registration, then you need first to register, if not, just write in the search box the name of the movie or desired program. If you do not know exactly what you want to fins, simply go to the category of movies or video, or games. Next, select a subcategory - Documentary, foreign, series and so on. The whole system is very similar in almost all trackers. So if you have used any other tracker and moved to a new one, you can understand a new one. After finding the desired movie, in its description may be present, such information:
Seeder is a user who distributes the entire downloaded file. Generally, the more seeds, the better, because thanks to them, upload speed is significantly increased. But even if there is no distribution, no oxide, it does not mean that you can not download the file.
Download torrent. PIR user who simply participate in the distributing.
Leech is a party distribution that a certain number of segments downloaded files and distributes them. The client program can find leech addresses, file segments as they have, and the speed with which they give and they take. But this does not mean that if there is no distribution of oxides, the leeches will not be able to get the file. Having a different number of segments, they can share them with each other until they get the whole file. Especially if a lot of leeches are available.
Let us summarize the information. In general, BitTorrent or simply torrent is an Internet protocol that allows you to quickly download large files. In contrast to the usual download site, using the BitTorrent file takes piece by piece in a large number of users. This allows you to download large files like music albums, movies and TV series much faster than would be obtained by means of other protocols torrent tracker.
To understand how BitTorrent works, it is worth considering what happens when we download a file from a site in a conventional manner. And there is something like this:
- The user opens a web page and clicks on the link to start downloading the file to the computer Download torrent ;
- The browser the client tells the server a computer with a desired file that you want to transfer a copy of the file to your computer;
- Runs through one of the transmission protocol a list of rules, such as FTP File Transfer Protocol or HTTP Hypertext Transfer Protocol.
In the data transmission, speed is affected by the set of factors, including the type of protocol, and the server load. If the file is a heavy and at the same popular time, server load is high and the speed of downloading, respectively, is low. torrent tracker.
When using torrents, the system is very different. The file is not downloaded from any server, and, as already mentioned, it is drawn in part from a plurality of users so we do not depend on the load on a single server and its availability. However, it will not work without the server. You need a torrent client - a special program for downloading and assembling the elements of the file together. BitTorrent works based on the principle you give me, I have what you have : it is accepted not only for downloading but also to distribute, and download speeds often depends on the upload speed it all depends on how this is principled about this torrent tracker. Here is how it works:
- User opens a torrent client special torrent-file - a tiny file that corresponds to the large files scattered on the internet;
- Torrent client reads torrent-file and binds said it tracker to find the computers where it is currently running as a client program, and you want us to have the entire file so-called LEDs, or siderite - seeds or part peers - peers, most of all, they, like us, are now busy downloading ;
- The tracker identifies the swarm of computers that have fragments or entire file and are in the process of downloading or distribution, and involves you in it;
- The tracker helps the client of software components share files with computers in the swarm, as a result your computer receives pieces of the file from different sources, and the client gathers them together,
- If you leave your bittorrent client running after the download is finished, you will be in a number of seeders and will be able to raise its rating on the tracker, to continue to download faster. At too low rating may apply different restrictions to download, for example, no more than one file at a time, or load may be temporarily forbidden for those who are trying to only receive, not handing out - for so-called leechers from the word leech.
Rating is a very commonly used tool to stimulate users to stay on hand, but there is a tracker, where the rating system is not applied torrent tracker.
It is noteworthy that the more popular the file is, the greater the oxides and the faster the download is note, if you boot from a traditional server situation is the opposite.
As you have already understood, installing, configuring and using the torrent client is very simple and useful. To download through BitTorrent, you must first install the program - a torrent client. You may also need to adjust the firewall settings if you use it, so that it is allowed to take the torrent files. But first things first:
- Download the torrent client, for example, site run the installation by double clicking on the icon the installation process intuitive, you can leave the default settings, and upon its completion the message about successful installation ;
- Be online, find a movie you want to download and open it in uTorrent;
- Wait for uTorrent to download movies, parallel distributing it in fragments;
- If desired, leave uTorrent running, ie remain on hand.
If the download of the film in our example does not start, then either now no one gives out it, or your firewall software that blocks unauthorized access to computer ports blocks the uTorrent. Go to the firewall settings and open ports from 6881 to 6889 for incoming traffic which uses them BitTorrent. You may also need to enable port forwarding IP-address of your computer to the port from 6881 to 6889, to other computers on a swarm might see you. Here, you may need professional help or more detailed acquaintance with the principles of the firewall settings bad advice - you can simply disable the firewall.
Features of the BitTorrent network. BitTorrent is different from similar P2P-protocol: for each distributed file, a file with extension torrent, which contains information about the distributed file. This torrent-file can be distributed through any channels of communication such as lists of torrent-files can be laid out on special Web servers located in the user s network, sent via email, posted to blogs or news feeds RSS. Itself torrent-file contains meta information for example, hash sum address tracker, and so on of the distributed data. These are distributed through its own communications protocol based on TCP / IP.
The basic principle of the record, the distribution file is completely controlled tracker whose address is in the torrent-file, so that users download the file itself called Leecher begins to distribute as soon as downloading is suitable for this first part. Cooperative user behavior is inherent in the very architecture of the protocol, and in principle can not be selfish.
Architecture of BitTorrent provides for a file, put in a network, the only owner who is interested in its propagation. The original owner of the file generates a torrent-file. The client, in turn, downloads a file for HTTP, FTP, or simply handing out any way with extension torrent, which contains information about the address of the owner, the name and size of the desired file and its hash. That s all you need to track the progress of the process, control and response capabilities users to download an incomplete or empty file.
The key to the success of any peer to peer network typically requires users not only upload files, but also to share them with others. Meanwhile, for various reasons mostly related to payment channels, quite often users prefer as soon as possible to download the file and shut, despite the fact that the rules of etiquette written request to share with other users. This reduces the amount of available sources, because of which suffer from stability and quality of the network. The BitTorrent provides a special method of dealing with selfish leeches, which involves the user rating, where the most generous given priority on foreign servers, and those who share unwilling boot Popular files go to the end of the queue.
Participation in the exchange system of tracker-server programmers BitTorrent gave an opportunity to introduce an algorithm that prevents the appearance of incomplete files. Since the tracker stores information about segments successfully loaded on each machine, the file download will start to force new customers with the most rare segment. If BitTorrent client downloads large files, divided into 200 parts, it does not mean that the process will begin with the segment number 01 and end segment. 200. The customer always receives the segment, which occupies the last place on the prevalence of that, ideally after 200 connections to the central the server will provide an opportunity to put in a peer entire file. torrent tracker.
Download Toshiba Satellite A200-ST2043. Toshiba Satellite A200-ST2043 Intel Graphics Driver 7.14. ST2043 Intel Display Driver Satellite A200-ST2043 Intel.
Satellite Pro A200. OR. ATI Display Driver Display: 8.38: Windows Vista 32-bit. Toshiba Component: 7.00.29: Windows Vista 32-bit.Toshiba Satellite A200 Drivers. Windows 7 32Bit Drivers. Display Driver – Download. 7 Comments to Toshiba Satellite A200 Windows 7 Drivers.
Satellite A200 32bit. TOSHIBA Extended Tiles for Windows Mobility. After upgrading to Windows 7, the latest driver and software updates will be provided via.
Here you can download the Windows 7 Drivers for Toshiba Satellite A200. Bluetooth Stack – Download Chip Set Utility – Download Display Driver – Download Fingerprint Software – Download LAN Driver – Download Modem Driver – Download Sound Driver – Download Webcam Driver – Download Audio Driver – Download CIR Driver – Download Realtek Wireless LAN Driver – Download Atheros Wireless LAN Driver – Download Hey there. This drives are for all models of Satellite A200.
This will reset all color values, set below.colors
Torrent Name AGE FILES SIZE; Udemy - How to Earn Extra Money and Supplement Your Income Create Courses - Make Money - A Simple How To Guide. Date: 01/21/16.

Big Download Portal. You can find and download evrething you want.
Shop Amazon s Gold Box for our Deal of the Day, Lightning Deals, and Best Deals, featuring hand-picked deals with low prices on top products updated daily.
Quilt Disappearing Nine Patch Pattern
Looking for your next project. You re going to love Disappearing 9-Patch Baby Quilt by designer Janice Ryan.
Privacy Policy / Your California Privacy Rights
Revised and posted as of March 4, 2013
Prime Publishing, LLC Company, we or us reserves the right to revise this Privacy Policy at any time simply by posting such revision, so we encourage you to review it periodically. In order to track any changes to this Privacy Policy, we will include a historical reference at the top of this document.
This Privacy Policy will tell you, among other things:
Your California privacy rights.
How we collect information and what information we collect.
Your choices regarding the sharing of information.
ACKNOWLEDGEMENT/YOUR AGREEMENT
Company websites are not intended for use by individuals under the age of 18 or those who are not legal residents of the United States. By using our website or submitting information to us, you consent to the Company s use and sharing of the information collected or submitted as described in this Privacy Policy. If you are not 18 years of age or older and a valid resident of the United States or you do not agree with the terms of this Privacy Policy, do not provide us with any information or use any of the products or services offered or provided on Company websites or through Company technology.
YOUR CALIFORNIA PRIVACY RIGHTS
Beginning January 1, 2005 under California s Shine the Light law, California residents who provide personal information in obtaining products or services for personal, family or household use are entitled to either: 1 a list detailing the categories of information shared and the entities to which such information was provided; or 2 to be notified of a mechanism by which a consumer may opt-out of having their information shared with third parties. We have elected the second option. To opt-out of having your information shared with third parties please write to us.
HOW DO WE COLLECT INFORMATION AND WHAT INFORMATION DO WE COLLECT.
We collect and combine personally identifiable information PII and non-personally identifiable information Non-PII through various sources, including those discussed below. For your reference, PII is data collected with an intention to specifically identify, contact or locate a person, including but not limited to name, address, telephone number, or e-mail address. Conversely, Non-PII is data that is not used to specifically identify, contact or locate an individual, including but not limited to zip code, gender, age, or IP address.
Website operators that license our ad serving technology pass information to us so that we may serve advertisements to you. The information passed may include, but is not limited to, your IP address, e-mail address, name, mailing address, telephone number, date of birth, and gender.
We also collect information about you when you complete a survey or offer form on one of our websites or web pages. This information may include, but is not limited to: your e-mail address, name, mailing address, telephone number, date of birth, gender, and payment information; information about your background, interests, health, education, career goals, and shopping preferences; and any other personal information or unique preference information you provide to us or our advertisers.
We collect information about you when you register on one of our websites. This registration information may include, but is not limited to your:
When you complete a registration or offer form that is hosted by one of our website publisher partners on our behalf, the website publisher partner may submit all or a portion of the information that you submitted on the form to the Company. This information may include, but is not limited to: your IP address, e-mail address, name, mailing address, telephone number, date of birth, gender, and payment information; information about your background, interests, health, education, career goals, and shopping preferences; and any other information you provide to our website publisher partner.
We may receive information about you, including but not limited to your IP address, e-mail address, first name, last name, mailing address, and telephone number, from third party marketing partners that provide us with consumer data to manage on their behalf.
Automatic Information/Digital Identifiers
We may automatically receive and store certain types of information about you through the data sources listed above.
You may be familiar with the term cookies, which are unique alphanumeric identifiers that store information on your computer. A cookie is placed on your computer when your web browser accesses our website. We use cookies for tracking transactions and the user characteristics explained in detail throughout this Privacy Policy. If you choose, there are utilities available for purchase from independent software providers to install on your computer as well as tools/preferences you can choose through most web browsers to make website visits anonymous. Of course, cookies let you have a more satisfying website experience, so we recommend that you leave them turned on.
We also collect information through our web server applications. This information includes your Internet Protocol or IP address, date/time stamp, browser type, and referring URL.
Additionally, we may use pixel tracking technology to track the completion of transactions with us or our advertisers, the source information for those transactions, and your IP address, date/time stamp, browser type, and referring URL.
The Company may be required to create, collect, maintain, and submit certain information required by the government, such as IRS Forms W-9 and 1099. This information, which may include your taxpayer identification number, will not be used, shared, transferred, or sold for marketing purposes.
HOW DO WE USE THIS INFORMATION.
We may use the collected PII and Non-PII for any legally permissible purpose in our sole discretion, including but not limited to those explained below.
We may serve advertisements to you based, in part, on your IP address, the demographic and geographic information you submitted to the Company during the website registration process, and other socio-economic information, psychographic information, Internet behavior i.e., browsing, search, shopping, purchase, and ad response behavior, and lifestyle information about you that we obtain from affiliated entities and from third parties.
We allow third-party companies to serve ads and/or collect certain anonymous information when you visit our Web site. These companies may use non-personally identifiable information e.g., click stream information, browser type, time and date, subject of advertisements clicked or scrolled over during your visits to this and other Web sites in order to provide advertisements about goods and services likely to be of greater interest to you. These companies typically use a cookie or third party web beacon to collect this information. To learn more about this behavioral advertising practice or to opt-out of this type of advertising, you can visit www.networkadvertising.org.
Our website technology may pre-select certain offers for you to view based on the demographic and geographic information you submitted to the Company during the website registration process. Additionally, this technology may pre-fill some or all of the offers data fields with the information you submitted during the website registration process in order to prevent you from having to re-enter this information. We may not show all of the pre-filled data fields to you.
We utilize customized post transactional or upsell technology to help advertisers generate sales, while providing you with a series of great offers we think may be of interest to you. The way it works is simple: once you purchase a product or service from one of our reward advertisers, you will be offered additional products or services that we think may be of interest to you. If you elect to purchase products or services from an advertiser in the post transactional channel, we will pass the information that you provided during the initial transaction to the subsequent advertiser, including but not limited to your credit card information. This information pass is done to enhance and simplify your purchasing experience. Your information will only be passed to an advertiser in the post transactional channel after you have elected to purchase their product or service. By electing to purchase their product or service you consent to the passing of your data to the third party advertiser in question.
Customer Service and Fulfillment
We may use your information to operate the website promotion, service your account and to fulfill rewards earned through Company websites. We may also use your information to verify your identity or claimed account status and, where we consider appropriate, investigate your compliance with the terms and conditions of the website promotion or any advertiser offer. We do retain customer service correspondence.
By submitting your credit card information to us or to one of our advertisers, you are authorizing the Company or its agent to periodically verify that your credit card account is valid and has credit available by charging, and thereafter crediting, a small sum to the card.
We may use your information in our online e.g., e-mail marketing and offline e.g., telemarketing, cell phone text messaging, skip tracing, and direct mail marketing programs. If you would like to be removed from these programs please write to us.
We may share the collected PII and Non-PII for any legally permissible purpose in our sole discretion, including but not limited to those explained below.
We may share information we collect with affiliated companies, including our parent company and other subsidiaries of our parent company, for use in their ad serving and marketing programs. This Privacy Policy does not apply to affiliated companies and their collection, use and sharing of information.
We may share your information with various third party vendors that are not part of the Company, including but not limited to vendors that provide us with technology to deploy commercial e-mail, vendors that sell the products or services for which you have qualified through one of our websites, and shipping companies that we utilize to ship products to you.
When you participate in an offer by completing a form, we will transfer the information you submitted on the form to the applicable advertiser.
When you answer yes or no to a marketing or survey question, some or all of the information that you submitted during the website registration process will be transferred to advertisers that we believe may be of interest to you without providing you with another opportunity to review the information.
When you select yes next to an offer, we will transfer some or all of the information that you submitted during the website registration process to the applicable advertiser without providing you with another opportunity to review the information.
We may use third party ad networks or ad serving companies to serve advertisements on our websites. We pass information about you to these companies so that they can deliver targeted advertisements that they believe will be of interest to you. The information passed to these companies may include, but is not limited to, your IP address, e-mail address, name, mailing address, telephone number, date of birth, gender, and any other information you provide to us. Web pages that are served by these companies will state that they are powered by or ads by the applicable company and will contain a link to that company s privacy policy.
Google, as a third party vendor, uses cookies to serve ads on our site.
Google s use of the DART cookie enables it to serve ads to our users based on their visit to our sites and other sites on the Internet.
Users may opt out of the use of the DART cookie by visiting the Google ad and content network privacy policy.
We may share, license or sell your information to third parties for various marketing purposes, including their online e.g., e-mail marketing and offline e.g., telemarketing, cell phone text messaging, skip tracing, and direct mail marketing programs. If you would like to be removed from these programs write to us.
Data Enhancement/Appending/Validation
We may use third party service providers to enhance our database with additional elements, including but not limited to age ranges present in your household, whether you own or rent a home, the length of time you have lived at your residence, whether you are a mail order buyer or responder, household income, and gender. Further, we may use third party service providers to append telephone numbers to other data points we have in our database. We also may use third party service providers to validate the data we have in our database.
Additionally, we may share, license or sell your information to third parties for use in their data validation, enhancement, information verification services, and, to the extent permitted by law, individual reference or look-up services.
Notwithstanding anything else in this policy, we or a data provider we have engaged may place or recognize a unique cookie on your browser to enable you to receive customized ads or content. These cookies contain no personally identifiable information. The cookies may reflect de-identified demographic or other data linked to data you voluntarily have submitted to us, e.g., your email address, that we may share with a data provider solely in hashed, non-human readable form. To opt-out of these cookies, please go to
Governmental Agencies or Other Companies
We may share your information with law enforcement officials or governmental agencies: 1 in response to their request; 2 when permitted or required by law; or 3 to establish our compliance with applicable laws, rules, regulations, or guidelines.
We may store and share your information with third parties for suppression or opt-out purposes.
We also may share your information with third parties when: 1 trying to protect against or prevent actual or potential fraud or unauthorized transactions; 2 investigating fraud that has already taken place; 3 enforcing or applying existing terms and conditions and/or other agreements; 4 protecting the rights, property or safety of our websites, our users or others; or 5 responding to subpoenas, court orders or legal process, or to establish or exercise our legal rights or defend against legal claims.
In all cases, this information is not provided to these entities or persons for marketing purposes.
Should the Company choose to sell or transfer business assets, it is possible that the information we possess may be transferred as part of that transaction. The Company may decide to retain a copy of the information post sale or transfer.
Marketing Communications and Unsubscribe Information
By completing and submitting a Company registration form, you are consenting to receive marketing communications from the Company and its third party marketing partners. If, after you have shared your information with the Company, you decide that you do not want to receive marketing communications or newsletters from the Company and its third party marketing partners, you can discontinue the communications by clicking here and filling out our form. If you have registered or submitted information under more than one e-mail account, you must submit separate unsubscribe requests for each account.
As it relates to marketing communications or any other questions you might have about our Privacy Policy, please write to us at Prime Publishing, LLC, 3400 Dundee Road, Suite 220, Northbrook, IL 60062.
WHAT HAPPENS IF I HIT A LINK TO ANOTHER SITE FROM A COMPANY WEBSITE.
Our websites may offer links to other websites. Other websites have their own terms of use and privacy and security policies. If you choose to visit one of these sites, you should review the policies that govern that particular site.
APPLICATION OF THIS PRIVACY POLICY
This Privacy Policy applies to all information collected by or submitted to the Company. Other affiliated entities of the Company may obtain information independently from transactions and experiences with you or from other sources. This Privacy Policy does not pertain to that information.
WHAT IS THE POLICY WITH RESPECT TO COMMUNICATING WITH CHILDREN.
We recognize the unique privacy concerns regarding children. We are committed to carefully protecting privacy where children are involved no matter the point of contact. In particular, our intention is to fully comply with the Children s Online Privacy Protection Act COPPA. Per COPPA guidelines, we do not knowingly collect PII from children under the age of 13. If a parent or guardian is made aware that a child under the age of 13 has provided us with PII through any point of contact, click here to contact us and we will delete the information about the child referenced from our files.
There is no such thing as complete security on the Internet or otherwise. The Company uses various security techniques on our websites to help protect against the loss, misuse or modification of information we ve collected from you. When you access your personal information or transmit information to us, that information is stored on servers that we have taken steps to protect from unauthorized access or intrusion. While we strive to protect your information, the Company cannot ensure or warrant the security of any information you transmit to us. You acknowledge and assume this risk when communicating with the Company, its partners and affiliates.
YOU UNDERSTAND AND AGREE THAT ANY DISPUTE OVER PRIVACY IS SUBJECT TO THE TERMS AND CONDITIONS OF THIS PRIVACY POLICY, AS WELL AS THE TERMS AND CONDITIONS OF THIS WEBSITE INCLUDING LIMITATIONS ON DAMAGES. YOU AGREE THAT THE COMPANY S LIABILITY FOR ANY BREACH OF THIS PRIVACY POLICY SHALL BE LIMITED TO THE VALUE OF THE TRANSACTIONS OR SERVICES PROVIDED TO YOU BY THE COMPANY TO THE EXTENT SUCH CLAIM IS NOT OTHERWISE BARRED BY OUR TERMS AND CONDITIONS.


About Split Nine Patch Quilt Blocks
Most split nine patch quilt and quilt block patterns show you how to cut and sew together individual squares and triangles, and others have quilters quick piece the half square triangle units that are used along each quilt block s diagonal.
This method is just a bit different, and allows you to strip piece the light and dark halves of the quilt block to make four identical block halves from straight strips of fabric.
It might seem a little confusing at first, but once you construct a block you ll see how fast and simple it is to finish a set.
You ll also see this quilt block referred to as Nine Patch Straight Furrows.
Read all of the instructions and examine the illustrations before you choose fabrics and begin sewing.Choose a Quilt SizeA 15-1/2 square quilt with 3 blocksA 30-1/2 square wallhanging with 6 blocks.
The split nine patch quilt I call Carolina Byways, above, reflects the up and down mountains in our part of the country. Both it and my Country Roads quilt were assembled with strip pieced split nine patch blocks.
Compare the quilts and you ll see how different the finished project can be when you vary fabrics and block arrangement. You can create many other layouts, too, such as the sunshine and shadows look of a log cabin quilt.
An assortment of scrappy fabrics works perfectly for a split nine patch quilt. Check the cutting instructions on page 2 to make sure your scraps are large enough.
Fabrics For the 15-1/2 Miniature QuiltDarks, 1/2 yardMedium Darks, 1/4 yardLights, 1/2 yardMedium Light Fabrics, 1/4 yard
Fabrics For the 30-1/2 QuiltDarks, 1/2 yardMedium Dark Fabrics, 1/4 yardLights, 1/2 yardMedium Lights, 1/4 yard
Backing: 5/8 yard for mini; 1-1/8 yards for larger quilt
Batting: 19 square for mini; 35 square for larger quilt
Binding, running inches: 72 for mini; 135 for larger quilt See How to Make Binding Strips for Quilts
Also see my Nine Patch Straight Furrows pattern for an alternative method that can be used to assemble these quilt blocks.
Use my Split Nine Patch quilt pattern to make a strip pieced quilt that can arranged into many different layout variations.
I m using hartfield by barbara brackman. it has 30 charms. lay out 9 different charms that you like together. don t forget to throw in some contrast.

I love the disappearing nine patch quilt pattern because it looks complicated, but is really so simple.
This has to be the clearest tutorial for disappearing nine patches that I ve come across. I m a new quilter and a DNP for my daughter is my next project.
Split Nine Patch Quilt Pattern
Mar 18, 2015 Disappearing Nine Patch Quilt History. First, a little history about the method used to create quilt blocks known as disappearing nine patch. The.


I love this technique. I have seen each of your blog posts about it. I can totally see how it is a disappearing 9 patch. I think it would be great to use for an I spy.